Security as a Platform
Unified visibility, real-time detection, and expert-led breach response.
Keeping Australian businesses connected, protected and ready for what’s next.
Security as a Platform
Security as a Platform includes the design,
implementation, and ongoing management of the following services:
- Endpoint Security
- Email Security
- Physical & Virtual Firewalls
- Secure Access Service Edge (SASE)
- Secure Browser
- SOC-as-a-Service
Phases
Security as a Platform includes three components:

1. Analyse
Gain full visibility across your
estate by stitching together
alerts from Endpoint, Cloud,
Identity, and Network Security
into a single view.

2. Detect
Alerts and logs are analysed in real-time against normal behaviour and the latest threat intelligence to detect breaches.

3. Respond
The elite SOC team proactively monitor the estate, and should a breach occur, will contain the threat, and resolve the issue in under an hour.
Benefits
The key benefits that Security as a Platform delivers are:

Consolidates alerts into a single view
Eliminates blind spots
Human expertise integrated with
automation
Faster Detection and Response
Unified visibility of the Attack Surface
World-class threat intelligence
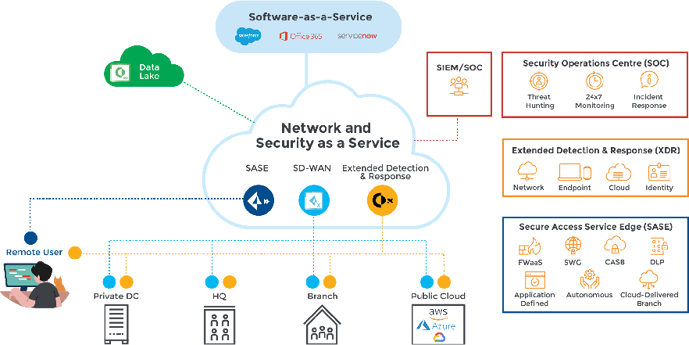
Security as a Platform building blocks
Protect your business with AI-powered endpoint and email security, secure access from anywhere, and real-time threat detection and response.
Get in touch
Get expert insights on connectivity and cybersecurity. Subscribe to the Enablis blog today.